Beware the Charger: Unveiling the latest stealthy hacker tool – The O․MG Elite cable
Is that phone charger a gateway for hackers?
Gadgets that break things: our favorite hacking hardware
In the intriguing realm of tech, not all gadgets are as benign as they appear. A profound revelation may strike you if you visit Def Con, a convention celebrated for its gathering of hacking aficionados. Among the myriad of innovations, the O.MG Cable stood out, redefining the perception of ordinary USB cables. This device isn’t just a cable; it’s a wolf in sheep’s clothing, boasting an unassuming design yet packed with capabilities that could very well be the envy of espionage enthusiasts.
It’s just a USB cable?
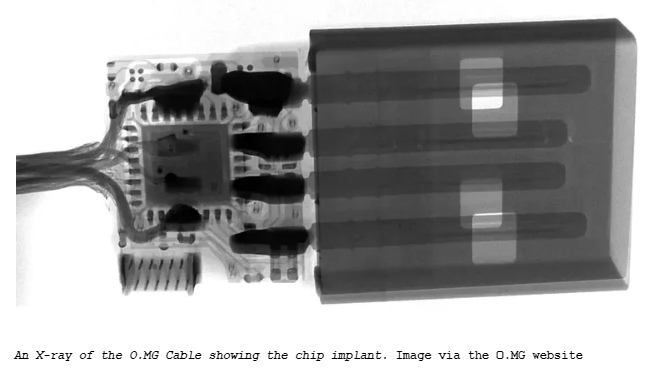
At first glance, the O.MG Cable mirrors every other USB cable you’ve encountered, but this facade is precisely what makes it formidable. Crafted by a developer known simply as MG, this cable harbors a secret—a miniature web server, USB communication features, and Wi-Fi connectivity, all tucked away within its slender form. Once connected, it springs to life, offering its wielder the power to monitor, command, and even extract data from unsuspecting devices.
What can it do?
Imagine a cable that, to the untrained eye, is just another tool for charging or data transfer. Yet, its capabilities are vast and alarming. With functionalities akin to the USB Rubber Ducky—a device I also had the chance to examine at Def Con—the O.MG Cable can execute keystroke injection attacks. This means it can pretend to be a keyboard, unleashing a barrage of commands that can compromise a target device. From downloading malicious software to capturing your most sensitive passwords, its stealth allows it to operate undetected.
Moreover, the cable includes a keylogger feature, capable of recording hundreds of thousands of keystrokes, ensuring that nothing typed through it escapes unnoticed. This could include passwords, personal messages, or any information inputted through a connected keyboard.
Are you at risk
What heightens the intrigue around the O.MG Cable is its built-in Wi-Fi capability. This allows it to bypass conventional security measures, enabling data theft even from devices that are disconnected from external networks. The thought alone is enough to unsettle anyone aware of the value of their digital privacy.
Despite its menacing potential, the cable’s creator assures that it is primarily a tool for professional penetration testing, priced at a point that discourages casual misuse. Yet, the existence of such a device serves as a stark reminder of the necessity for vigilance in our digital interactions.
Could I use it myself?
While I didn’t personally test the O.MG Cable, insights into its operation suggest that it doesn’t require extensive technical know-how to deploy. Initial setup involves firmware updates and programming through a browser-based interface, with scripts written in a variant of DuckyScript—a language shared with the USB Rubber Ducky. This accessibility means that, with some dedication, even those with a rudimentary understanding of technology could harness its potential.
A Call for Caution
The O.MG Cable epitomizes the double-edged nature of technological advancement. While it’s a testament to human ingenuity, it also highlights the growing need for awareness and caution in our increasingly connected world. Whether you’re a tech enthusiast or simply someone concerned with safeguarding your digital footprint, the message is clear: not all chargers are created equal, and sometimes, the most innocuous devices can harbor the greatest threats.
FAQs
What makes the O.MG Cable different from regular USB cables?
- The O.MG Cable is designed to look and function like a standard USB cable but harbors hidden hacking capabilities, including data interception and remote command execution.
Can the O.MG Cable really hack any device?
- While it has the potential to compromise many devices through keystroke injection and data exfiltration, its effectiveness depends on the target’s security measures and the attacker’s intentions.
Is it legal to own an O.MG Cable?
- Ownership itself isn’t illegal, but using the cable for unauthorized access or data theft is against the law and ethical guidelines.
How can I protect myself against threats like the O.MG Cable?
- Stay informed about the latest security threats, scrutinize the origins of your tech accessories, and implement robust digital security practices.
Where can I learn more about cybersecurity and protecting against hacking tools?
- Cybersecurity resources and forums, reputable tech news outlets, and official cybersecurity organizations are excellent sources of information.








