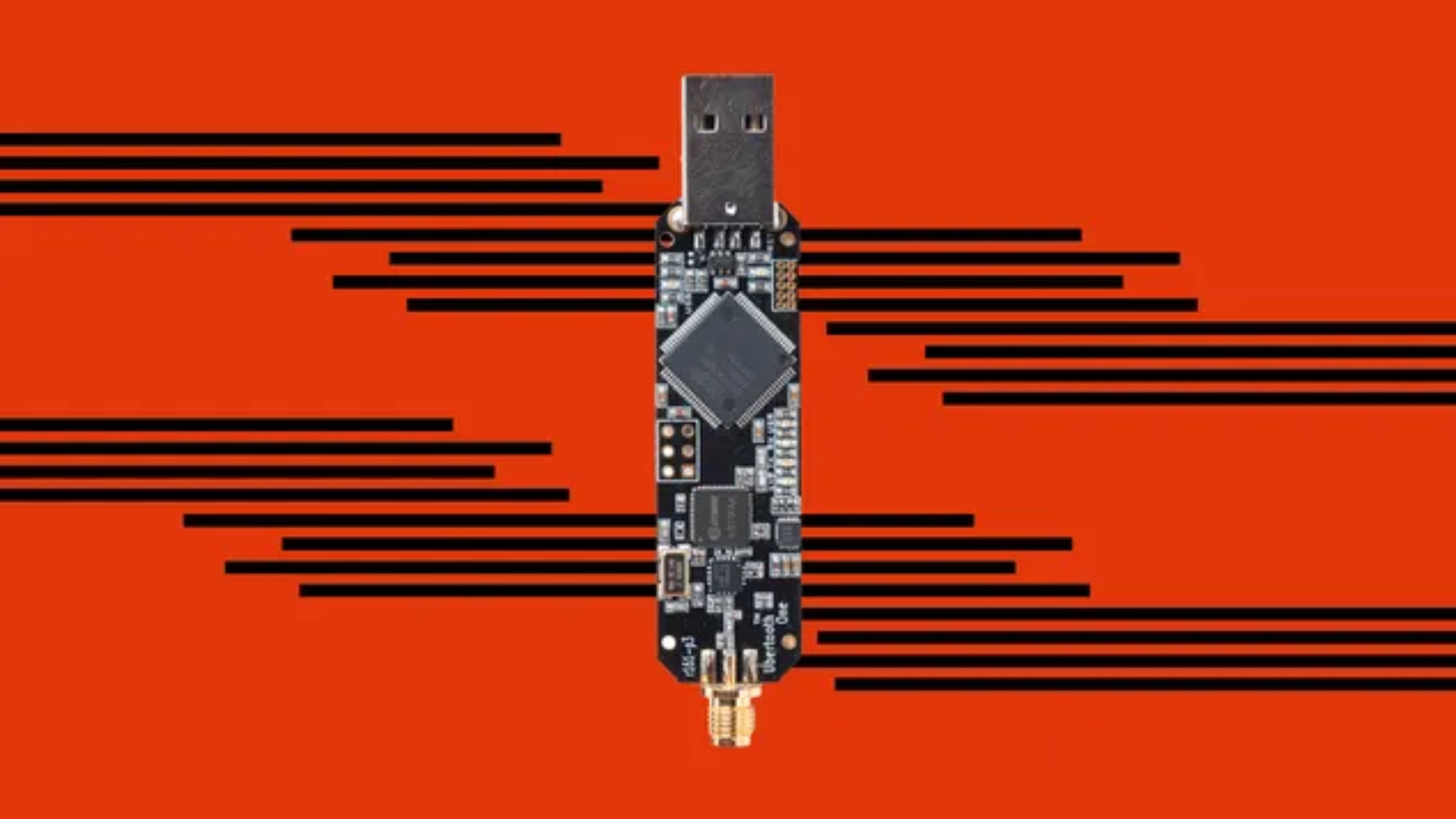
Ubertooth One emerges as a cutting-edge, open-source platform tailored for 2.4 GHz wireless development, specifically engineered for those keen on delving into Bluetooth technology.
In the dynamic landscape of digital security, the team embarked on a mission to scrutinize the communication between embedded devices in a product, aiming to verify their encryption integrity and resilience against radio frequency-based threats like jamming, GPS spoofing, and replay attacks.
Dive into the world of RFID security with the latest innovation from RRG – the Proxmark 3 RDV4.01. Crafted in collaboration with renowned names like Proxgrind, Iceman, and 0xFFFF, this device stands out as the pinnacle of RFID tools for security experts everywhere.
Digital connectivity forms the backbone of our daily lives –understanding and securing wireless communication is paramount. Devices ranging from smartphones and Wi-Fi routers to contactless payment systems operate on diverse wireless frequencies, highlighting the complexity of modern digital ecosystems. Navigating this intricate world has traditionally been the domain of cybersecurity experts, but the advent of the Flipper Zero device is bridging the gap, offering a tool that appeals to both cybersecurity professionals and hackers with a penchant for exploration.
In the intriguing realm of tech, not all gadgets are as benign as they appear. A profound revelation may strike you if you visit Def Con, a convention celebrated for its gathering of hacking aficionados. Among the myriad of innovations
In today’s fast-paced digital landscape, businesses are constantly seeking ways to enhance their software development processes and bolster their IT operations. The answer to this challenge lies in DevOps – a transformative approach that melds the worlds of software development and IT operations, enabling collaboration, streamlining processes, and ultimately revolutionizing the way companies deliver software. […]
Cybersecurity is a crucial component for businesses in the digital age. As technology advances, the threat landscape evolves, making cybersecurity more important than ever. Here are the top five reasons why every business should prioritize implementing robust cybersecurity measures: In conclusion, cybersecurity is no longer an optional extra but a fundamental necessity for businesses in […]